A recent Ponemon Institute survey of 675 security professionals in North America, Europe, the Middle East and Africa confirmed that security professionals in retail organizations are most concerned about advanced threats (AT). Yet even in the wake of unprecedented data breaches at companies like Target and Home Depot, most retail companies have just begun to make the investments in security operations staff and forensic tools needed to investigate security incidents in a timely and effective manner.
Instead, too many retailers continue to rely on “gut” feel to determine if they’ve have been the victim of a targeted attack. Only 34 percent have implemented formal incident response procedures, and 31 percent found DDoS attacks only via forensic evidence after the degradation of application or system performance.
The Ponemon survey confirmed that retail security operations teams are struggling, particularly at detecting and containing ATs once inside their network. Given their current resources, it takes on average 197 days to detect an AT — a significant dwell time for compromising a system and data theft. And though the respondents averaged “only” 81 incidents a month, couple that with the dwell time and how long it takes to contain an AT — 39 days on average — and you can understand how security operations teams perceive they're falling behind.
While many organizations are taking specific steps to strengthen their ability to detect and contain attacks moving forward, only 29 percent of the companies surveyed expect this to improve over the next 12 months.
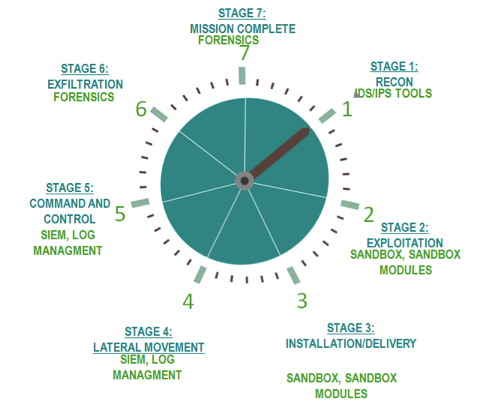
Disrupting ATs at Different Stages of the Cyber Kill Chain
The vast majority of respondents (76 percent) were familiar with the phrase "cyber kill chain" in relation to their companies’ experience and allocation of security resources. The kill chain refers to a lifecycle approach to threats that allows security professionals to more proactively remediate and mitigate ATs.
Respondents believe it was difficult to proactively disrupt ATs at any stage in the kill chain, but the majority (87 percent) singled out the very first stage — reconnaissance — as the most challenging. Installation of AT malware or action on objectives (e.g., data exfiltration) is the next most difficult phase to detect and disrupt.
Significantly, nearly two-thirds of the respondents (64 percent) said the most promising technology to stop ATs in the cyber kill chain is better intelligence about network traffic. Indeed, due to the lack of in-house intelligence and expertise, 28 percent of DDoS attacks were identified with shared intelligence from customers or partners.
Changing Budgets and Strategies for Disrupting ATs
Of the companies represented in the study, the average number of employees responsible for cybersecurity incidents was 11, with about 8 percent of the average total IT budget allocated to IT security activities and investments. Of that 8 percent of the total IT budget, approximately 34 percent is spent on technologies and 37 percent on in-house personnel.
A significant portion, roughly 22 percent of the IT security budget, is spent on cyber kill chain activities. However, ironically, the very least amount (2 percent) is spent on disrupting the most challenging phase: reconnaissance. It's in disrupting these early stages of reconnaissance and weaponization that any organization stands the best chance of getting out in front of ATs. In contrast, the most resources (20 percent) are currently spent on reacting after the weapon is delivered — the exploitation phase.
The majority of organizations (53 percent and 58 percent, respectively) use mean time to identify (MTTI) and mean time to contain (MTTC) metrics to determine the effectiveness of their incident response and containment processes. Not surprisingly, it takes IT staff considerably longer to detect and contain ATs, designed to be stealthy, than it does DDoS attacks. As mentioned above, the MTTI for ATs for the retail respondents (i.e., average dwell time) is 197 days. And just as damaging, the MTTC for an AT attack is approximately 39 days.
Retailers are aware of this race against time and are taking steps to improve their ability to detect and contain attacks more quickly. Most importantly, retail organizations are recognizing the value of better applied threat intelligence to improve their MTTI and MTTC metrics. About 60 percent are integrating threat intelligence into their incident response processes.
Additionally, 64 percent of respondents view technologies that provide intelligence about networks and traffic as most promising at stopping or minimizing ATs during the seven phases of the kill chain. No matter how much the threats, tactics and targets change, insight into networks and traffic are viewed as the critical first step to detecting ATs in your network.
About 40 percent of the companies surveyed are also looking to increase the size of their security operations staff. The skill sets and goals of these new resources are key. It's significant that these new resources are being tasked to proactively look for and find threats earlier in the kill chain. About one-third of the organizations in the survey are introducing hunting teams with the goal of reducing their MTTI and MTTC metrics.
Yet the findings clearly indicate more needs to be done. For example, while understanding that a broader context can help them spot and contain attacks more quickly, only 17 percent have moved to share threat intelligence with other companies or government entities.
Food for Thought
The integration of broader threat intelligence into incident response and the advent of security teams tasked to proactively hunt for threats earlier in the kill chain represent a new type of security strategy. Where are you investing in security solutions? What kind of balance are you attempting to create between technology and the people who use it? This study will let you assess your level of preparedness against ATs and DDoS attacks vs. those of your colleagues around the world. It also points to the some of the steps you can take to strengthen your security posture.
Arabella Hallawell is the vice president of corporate strategy at Arbor Networks, a provider of network security and network monitoring software.
Related story: Application Security Taking Center Stage for Retailers